Exploring the World: Travel Insights
Your go-to source for travel tips, destination guides, and cultural insights.
Veils of Digital Cash: Navigating Anonymity in Crypto Platforms
Uncover the secrets of digital cash! Explore how to maintain anonymity in cryptocurrency platforms and navigate the complex landscape of crypto privacy.
Understanding the Mechanics of Anonymity in Cryptocurrency Transactions
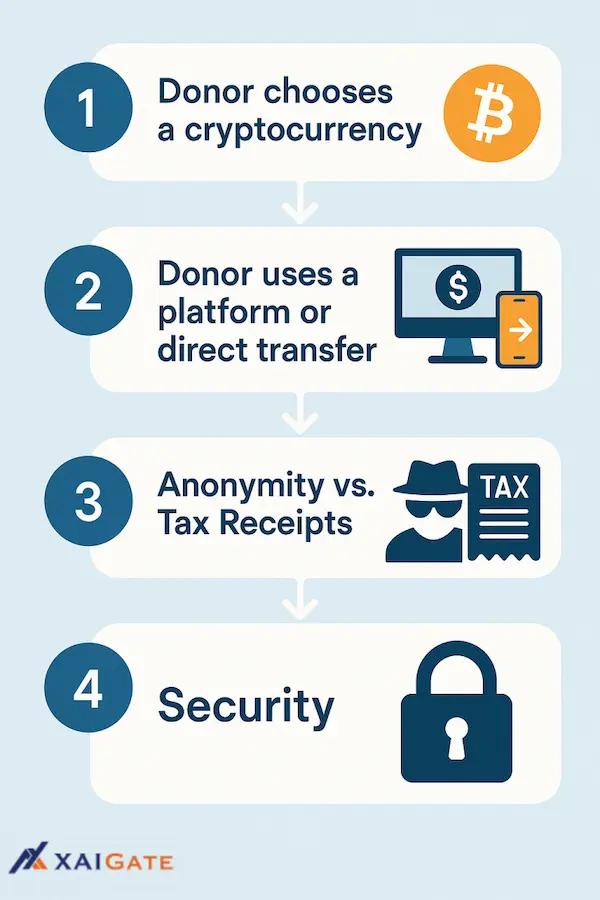
In the world of cryptocurrency, anonymity plays a crucial role in safeguarding user privacy and preventing unwanted surveillance. Understanding the mechanics of how anonymity is achieved in cryptocurrency transactions involves examining various technologies and practices. Most cryptocurrencies, like Bitcoin, offer a degree of pseudonymity, meaning that while transactions are recorded on a public ledger, the identities behind wallet addresses remain obscured. However, sophisticated tracking techniques can sometimes link these addresses to real-world identities, prompting the development of more advanced privacy-centric cryptocurrencies such as Monero and Zcash that implement anonymity through advanced cryptographic methods such as ring signatures and zk-SNARKs.
Additionally, the use of mixing services or tumblers has become popular among cryptocurrency users seeking enhanced anonymity. These services allow individuals to combine their coins with those of other users, effectively obfuscating the transaction trails that could otherwise lead back to them. While these methods provide an additional layer of privacy, users must also consider the legal implications and risks associated with utilizing such services. Overall, as the demand for anonymity in digital transactions continues to grow, understanding these mechanics not only informs users about enhancing their safety but also assists policymakers in addressing potential regulatory challenges in the ever-evolving cryptocurrency landscape.
Counter-Strike is a popular first-person shooter game that emphasizes teamwork and strategy. Players join one of two teams, terrorists or counter-terrorists, and engage in various gameplay modes. Many fans of the game also enjoy visiting the online casino scene, where they can find a cryptocasino.com promo code for exciting bonuses and promotions.
The Pros and Cons of Using Privacy Coins: What You Need to Know
Privacy coins have gained popularity as a means of enhancing financial confidentiality. One significant advantage is their ability to provide users with anonymous transactions, which can be crucial for those seeking to protect their identity and financial activities from public scrutiny. Additionally, these coins often employ advanced cryptographic techniques, such as ring signatures and stealth addresses, to obfuscate transaction details, making it nearly impossible to trace funds back to their origin. This level of anonymity can empower individuals in oppressive regimes or those who prefer to keep their financial affairs private.
However, the use of privacy coins isn't without its drawbacks. One major concern is their potential association with illicit activities, as the anonymity they provide can facilitate money laundering and other criminal enterprises. This scrutiny has led to increased regulatory challenges, with some governments contemplating or implementing bans on these currencies. Furthermore, the lack of transparency in transactions can make privacy coins less appealing to legitimate businesses that require compliance with financial regulations. Thus, while they offer substantial privacy benefits, users must carefully weigh these factors against the possible legal implications.
How Do Crypto Platforms Ensure User Anonymity? A Deep Dive
In the ever-evolving landscape of cryptocurrency, ensuring user anonymity is paramount for both safety and privacy. Crypto platforms implement several techniques to protect user identities, primarily by utilizing blockchain technology. Unlike traditional financial systems, which require personal information for transactions, blockchain operates on a decentralized network where transactions are recorded in a public ledger. To enhance anonymity, many platforms use a technique called coin mixing or tumbling, which obscures the transaction trail by blending various transactions together. This disrupts the possibility of tracing transactions back to individual users, thus fortifying their anonymity.
Additionally, many crypto platforms adopt the use of privacy coins like Monero or Zcash, which are specifically designed to provide enhanced anonymity features. These coins utilize advanced cryptographic techniques such as ring signatures and zero-knowledge proofs to ensure that transactions cannot be traced back to their origin. Furthermore, some platforms encourage the use of virtual private networks (VPNs) and Tor to mask user IP addresses, adding another layer of protection. Together, these strategies illustrate the vital efforts that crypto platforms make to foster an environment where user anonymity reigns supreme, allowing users to explore their digital financial freedom without the fear of surveillance.