Exploring the World: Travel Insights
Your go-to source for travel tips, destination guides, and cultural insights.
Data Transfer: The Secret Life of Your Bits and Bytes
Discover the hidden journey of your data! Uncover the secrets of bits and bytes in our deep dive into data transfer magic.
Understanding Data Transfer: How Your Bits and Bytes Travel Across the Internet
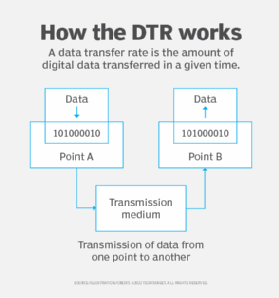
In today's digital age, understanding how data transfer works is essential for anyone who uses the Internet. At its core, data transfer involves the movement of bits and bytes—small units of data—from one point to another through various networks. When you send an email, stream a movie, or browse a website, your computer communicates with servers across the globe, utilizing a set of protocols and technologies designed for efficient transmission. This journey includes several stages, starting from your device's request to the server's response, encompassing routers, switches, and cables that facilitate the transfer.
The process of data transfer can be visualized as follows:
- Request initiation: Your device sends a request to access certain data, like a webpage.
- Routing: This request travels through multiple routers and switches, which direct it toward its destination.
- Data packaging: Data is divided into packets, ensuring it can be easily managed and transmitted.
- Delivery: Finally, the packets reach their destination server, where they are reassembled and sent back to your device.
If you're looking for efficient ways to manage multiple USB devices, check out the Top 10 USB Switch Selectors that cater to various needs and budgets. These selectors allow seamless switching between devices, making your workflow much more efficient. Whether you need to connect printers, scanners, or other peripherals, these top-rated options offer reliable performance and convenience.
The Journey of Data: From Your Device to the Cloud and Back
The journey of data begins the moment you create or interact with information on your device. When you send an email, upload a photo, or save a document, your data is first processed by your local device. This data is then packaged into packets, which are small units of data that can be easily transmitted over networks. These packets travel through various channels, from your home Wi-Fi or cellular network, heading towards the cloud. In the cloud, your data is stored on remote servers, where it can be accessed, processed, and analyzed by applications and services designed to enhance your digital experience. This seamless exchange allows for powerful functionalities such as real-time collaboration and instant access from anywhere in the world.
Once your data is in the cloud, it undergoes a series of transformations that enrich its value. Services leverage advanced algorithms to analyze and organize this data, enabling personalized experiences and insights tailored to your needs. When you retrieve your information, the process reverses. The data packets are sent back to your device, where they are reassembled into their original form. This journey of data not only highlights the efficiency of modern technology but also the importance of data security during transmission. With encryption and other security measures in place, you can rest assured that your information remains protected every step of the way.
What Happens to Your Data During Transfer? Unpacking the Process
When data is transferred over the internet, it undergoes a complex process that ensures its integrity and security. Initially, the data is packaged into small units called packets, each containing a portion of the overall information. These packets are then sent through networks, which may include routers and switches, that help manage the flow of data. During this transfer, multiple protocols, such as TCP/IP, come into play to maintain a reliable connection and ensure that all packets arrive at their destination without errors.
Once the packets reach their destination, the receiving device begins reassembling the data into its original format. This involves checking for any losses or errors that may have occurred during transfer. If any packets are missing or corrupted, the system requests retransmission of those specific packets. This meticulous process emphasizes how crucial it is to maintain data integrity during transfer. Additionally, encryption is often employed to protect sensitive information, ensuring that only authorized parties can access the data, thereby safeguarding against potential breaches.